Table of contents
Introduction
When transitioning to the cloud, numerous aspects require consideration, with security standing out as a pivotal concern, particularly in terms of authentication and authorization.
Authentication involves validating that an entity (user, service, application, etc.) is indeed the entity it claims to be, based on the provided information.
Various authentication methods exist, including password-based, certificate-based, biometric, token-based, one-time, push notification, voice, two-factor, multifactor, and more. Additionally, numerous authentication protocols are in use, such as PAP (Password Authentication Protocol), CHAP (Challenge-Handshake Authentication Protocol), EAP (Extensible Authentication Protocol), TACACS+, Kerberos, SAML, and others.
This article focuses on selecting the appropriate authentication solution for transitioning to the cloud, particularly for a .Net Framework application utilizing Kerberos.
Kerberos
Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography.
For the authentication, it relies on the components below:
Client: The device a user is trying to access a service from
Server: The computer or service the user wants to access
Key Distribution Center: A trusted third-party service with two parts:
Authentication Server (AS): Verifies user identities and issues Ticket Granting Tickets (TGTs)
Ticket Granting Service (TGS): Issues service tickets based on the TGT.
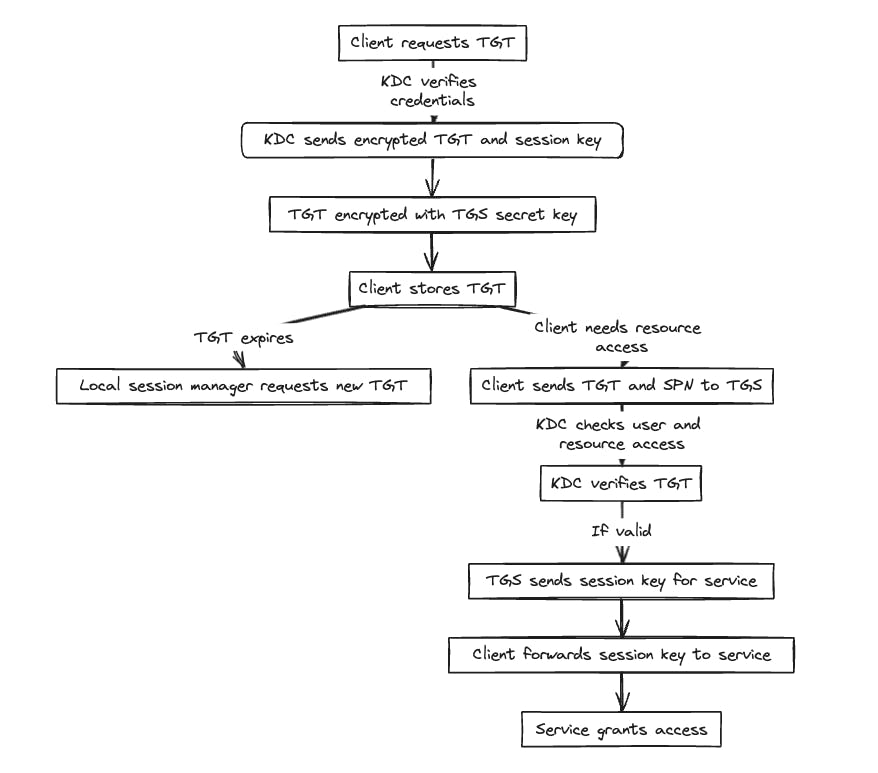
The authentication process consists of the following steps:
The client requests a TGT from the KDC;
The KDC verifies the credentials and sends back an encrypted TGT and session key;
The TGT is encrypted using the TGS secret key;
The client stores the TGT and when it expires the local session manager will request another TGT (transparent to the user);
The client sends the current TGT to the TGS with the Service Principal Name (SPN) of the resources the client wants to access;
The KDC verifies the TGT of the user and that the user has access to the service;
TGS sends a valid session session key for the service to the client;
The client forwards the session key to the service to prove the user has access and the service grand access.
Pros and Cons
Kerberos’s benefits are :
Access Control: The Kerberos authentication protocol enables effective access control by providing a centralized authentication server that verifies the identity of users and services.
Mutual Authentication: Kerberos authentication allows both service systems and users to mutually authenticate each other, ensuring that both parties can trust each other's identities.
Limited Ticket Lifetime: Each ticket in Kerberos contains timestamps and lifetime data, allowing administrators to control the duration of authentication and reduce the risk of unauthorized access.
Reusable Authentication: Kerberos authentication provides durable and reusable tickets, allowing users to access multiple services without needing to reauthenticate for each service.
Security: Kerberos ensures security through the use of multiple secret keys, third-party authorization, and cryptography. Passwords are not transmitted over the network, and secret keys are encrypted, making it challenging for attackers to impersonate users or services.
Kerberos's limitations are :
Single Point of Failure: The Key Distribution Center (KDC) represents a single point of failure. If the KDC is compromised, the entire authentication system is at risk, emphasizing the need for robust security measures to protect the KDC.
Time Synchronization: Kerberos requires all participating entities to have synchronized clocks. Failure to maintain time synchronization can lead to authentication failures or security vulnerabilities, highlighting the importance of time synchronization for the proper functioning of the Kerberos protocol.
Ticket Expiry: Once a user obtains a ticket from the KDC, it remains valid until it expires. If an attacker manages to steal a ticket, they can use it until it expires, potentially causing security issues. This emphasizes the need for strict ticket management and monitoring to mitigate the risk of unauthorized ticket usage.
Password Guessing: Like any system relying on passwords, Kerberos is vulnerable to password-guessing attacks if weak passwords are used. Implementing strong password policies and multifactor authentication can help mitigate this vulnerability.
Trusting the KDC: All entities in a Kerberos environment must trust the KDC. If the KDC is compromised, this trust is violated, leading to potential security breaches. It's essential to implement additional security measures and best practices to mitigate the impact of a compromised KDC.
Cloud Migration
As we migrate to the cloud, Kerberos faces limitations due to its architecture and its specialized environment, as it is not as widely integrated as SAML, OAuth, or OpenID.
The main limitations of retaining Kerberos as the authentication system when moving to the cloud are:
Single Point of Failure:*(explained above)*.
Network Latency and Connectivity: Communication between client and server across different networks or cloud providers may introduce network latency, potential connectivity issues, and increased complexity in routing and firewall configurations.
Time Synchronization: Maintaining time synchronization across distributed cloud resources and services can be challenging, leading to potential authentication failures and security vulnerabilities.
Trust Boundaries and Interoperability: Establishing and maintaining trust relationships between the client and server across different networks or cloud providers can be complex, requiring careful consideration of trust boundaries and interoperability.
Integration with Cloud Identity Services: Integrating Kerberos authentication with cloud identity services may require careful planning and configuration to ensure seamless interoperability and compatibility with cloud environments.
Conclusion
The limitations of Kerberos authentication become more pronounced when transitioning to the cloud, especially in public, private, or hybrid cloud environments. Challenges such as single points of failure, network latency, time synchronization, trust boundaries, and integration with cloud identity services can impact the effectiveness and security of Kerberos in the cloud.
In the next article, we will explore alternative authentication solutions that address these limitations and are better suited for cloud environments. We will delve into modern authentication protocols such as SAML, OAuth, and OpenID.
sources :

